Many times every day (about 5 times every day) I use context menu on tabs in order to restore my saved layouts of tabs. Most of the time it works perfect. But sometimes (1-3 times every week) I get crash of DO direct after restore of layout.
Today I had new effect after crash:
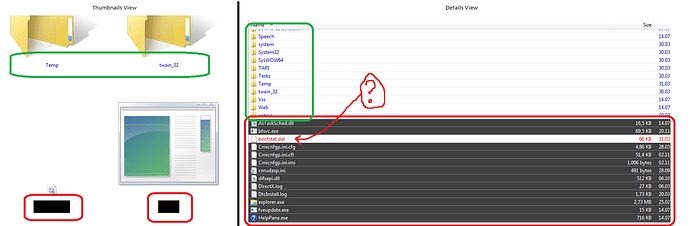
Details view:
Rows of files have now gray (#404040 ) back color. Folders are normal with white back color.
Thumbnails view:
Names of files have now black (#000000 ) back color. So I don't see the name now because text has black text color to. Like in details view no changes for folders.
Like every time I did not select to save anything at crash, so I don't understand why some color was changed.
Following settings I needed to change in order to restore default colors:
Display \ Colors and Fonts \ File and Folder Colors \ File and Fonders
Values after crash:
Values after manual restore:
Why values were switched after / at crash I don't know, but now I can see names of files without problems.
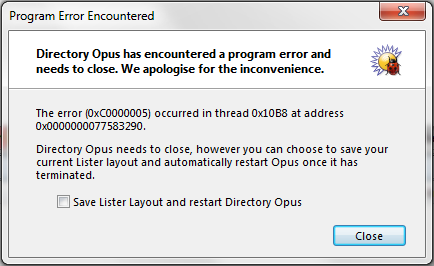
Sorry, I had forgot to attach crash dialog: ACCESS_VIOLATION
I have looked into the dumps and found many times the same stacktrace:
> ntdll.dll!RtlSizeHeap()
shell32.dll!CTCoAllocPolicy::_CoTaskMemSize(void *)
shell32.dll!ILClone()
shell32.dll!GetCurFolderImpl()
shell32.dll!_GetIDListFromObjectWorker(struct IUnknown *,struct _ITEMIDLIST_ABSOLUTE * *)
shell32.dll!SHGetIDListFromObject()
shell32.dll!CRegFolder::_GetFolderIDList(void)
shell32.dll!CRegFolder::_CreateCachedRegFolder(struct IDLREGITEM const *,struct IBindCtx *,struct _GUID const &,void * *)
shell32.dll!CRegFolder::_BindToItem(struct IDLREGITEM const *,struct IBindCtx *,struct _GUID const &,void * *,int)
shell32.dll!CRegFolder::BindToObject(struct _ITEMIDLIST_RELATIVE const *,struct IBindCtx *,struct _GUID const &,void * *)
shell32.dll!SHBindToObject()
shell32.dll!CDesktopFolder::_GetFolderForParsing(unsigned short const *,struct IBindCtx *,struct IShellFolder * *,struct _ITEMIDLIST_ABSOLUTE * *)
shell32.dll!CDesktopFolder::ParseDisplayName(struct HWND__ *,struct IBindCtx *,unsigned short *,unsigned long *,struct _ITEMIDLIST_RELATIVE * *,unsigned long *)
shell32.dll!CRegFolder::ParseDisplayName(struct HWND__ *,struct IBindCtx *,unsigned short *,unsigned long *,struct _ITEMIDLIST_RELATIVE * *,unsigned long *)
dopus.exe!000000013f821c4a()
Leo
April 2, 2014, 9:55pm
5
That stack suggests that something has corrupted the shared memory heap used by the shell (among other things).
Unfortunately, what usually happens it that something corrupts the heap but doesn't cause a crash, and then a moment later some other innocent code tries to use the heap and crashes because it is corrupt. So the stack trace probably isn't showing the guilty code/component.
If something is corrupting the heap, or corrupting memory in general, it could also explain the other strange behaviours. (All bets are off at that stage, basically.)
The problem is most likely to be caused by a shell extension, and the Crash, exit or high CPU when viewing certain directories guide has suggestions on how to track it down.
I'm assuming that you're happy with fairly technical tools, since you were able to get the stacktrace. If so, you may also want to try using PageHeap. PageHeap will often catch the corruption the moment it happens, causing a crash as soon as the mess is made rather than when something else trips over the mess, and thus generating a stacktrace which points to the likely culprit. Details on enabling PageHeap can be found here: Re: Dopus Rename/Copy Crash .
(If you use PageHeap, remember to turn it off and restart Opus afterwards, since it can significantly slow down the process due to all the extra checks it performs.)
At the moment I have enabled PageHeap and attached WinDbg to DO.
I still get exceptions. For example like this:
Sun Apr 6 09:08:00.509 2014 (UTC + 2:00): ModLoad: 000007fe`f2020000 000007fe`f20f5000 C:\Program Files\GPSoftware\Directory Opus\VFSPlugins\opus7zip.dll
Sun Apr 6 09:08:00.511 2014 (UTC + 2:00): ModLoad: 000007fe`fd9c0000 000007fe`fda57000 C:\Windows\system32\COMDLG32.dll
Sun Apr 6 09:16:58.938 2014 (UTC + 2:00): ModLoad: 000007fe`f3050000 000007fe`f3125000 C:\Program Files\GPSoftware\Directory Opus\VFSPlugins\opus7zip.dll
Sun Apr 6 09:16:58.940 2014 (UTC + 2:00): ModLoad: 000007fe`fd9c0000 000007fe`fda57000 C:\Windows\system32\COMDLG32.dll
Sun Apr 6 09:17:15.595 2014 (UTC + 2:00): ModLoad: 000007fe`f9b90000 000007fe`f9baf000 C:\Windows\system32\thumbcache.dll
Sun Apr 6 09:17:15.668 2014 (UTC + 2:00): ModLoad: 000007fe`fcab0000 000007fe`fcacf000 C:\Windows\system32\thumbcache.dll
Sun Apr 6 09:17:15.682 2014 (UTC + 2:00): ModLoad: 000007fe`f9b90000 000007fe`f9baf000 C:\Windows\system32\thumbcache.dll
Sun Apr 6 09:17:15.692 2014 (UTC + 2:00): ModLoad: 000007fe`fcab0000 000007fe`fcacf000 C:\Windows\system32\thumbcache.dll
Sun Apr 6 09:17:15.719 2014 (UTC + 2:00): ModLoad: 000007fe`f9b90000 000007fe`f9baf000 C:\Windows\system32\thumbcache.dll
Sun Apr 6 09:17:15.733 2014 (UTC + 2:00): ModLoad: 000007fe`fcab0000 000007fe`fcacf000 C:\Windows\system32\thumbcache.dll
Sun Apr 6 09:17:33.307 2014 (UTC + 2:00): (880.f64): Access violation - code c0000005 (first chance)
First chance exceptions are reported before any exception handling.
This exception may be expected and handled.
*** ERROR: Symbol file could not be found. Defaulted to export symbols for C:\Program Files\GPSoftware\Directory Opus\dopus.exe -
dopus+0x48f632:
00000001`3feff632 f0ff4b08 lock dec dword ptr [rbx+8] ds:00000000`36058f88=????????
*** ERROR: Symbol file could not be found. Defaulted to export symbols for C:\Program Files\GPSoftware\Directory Opus\dopuslib.dll -
# Child-SP RetAddr Call Site
00 00000000`2c58f130 00000001`3fefa6db dopus+0x48f632
01 00000000`2c58f160 00000001`3fef3dfe dopus+0x48a6db
02 00000000`2c58f1b0 00000000`77319bd1 dopus+0x483dfe
03 00000000`2c58f200 00000000`77313bfc user32!UserCallWinProcCheckWow+0x1ad
04 00000000`2c58f2c0 00000000`77313b78 user32!CallWindowProcAorW+0xdc
05 00000000`2c58f310 000007fe`fbd56215 user32!CallWindowProcW+0x18
06 00000000`2c58f350 000007fe`fbd569a0 COMCTL32!CallOriginalWndProc+0x1d
07 00000000`2c58f390 000007fe`fbd56768 COMCTL32!CallNextSubclassProc+0x8c
08 00000000`2c58f410 00000001`3fae66d1 COMCTL32!DefSubclassProc+0x7c
09 00000000`2c58f460 00000001`3fba213e dopus+0x766d1
0a 00000000`2c58f4b0 000007fe`fbd569a0 dopus+0x13213e
0b 00000000`2c58f500 000007fe`fbd56768 COMCTL32!CallNextSubclassProc+0x8c
0c 00000000`2c58f580 00000001`3fae66d1 COMCTL32!DefSubclassProc+0x7c
0d 00000000`2c58f5d0 00000001`3fba39d4 dopus+0x766d1
0e 00000000`2c58f620 00000000`77319bd1 dopus+0x1339d4
0f 00000000`2c58f6a0 00000000`77313bfc user32!UserCallWinProcCheckWow+0x1ad
10 00000000`2c58f760 00000000`77313b78 user32!CallWindowProcAorW+0xdc
11 00000000`2c58f7b0 000007fe`fbd569a0 user32!CallWindowProcW+0x18
12 00000000`2c58f7f0 000007fe`fbd56768 COMCTL32!CallNextSubclassProc+0x8c
13 00000000`2c58f870 00000001`3fae66d1 COMCTL32!DefSubclassProc+0x7c
14 00000000`2c58f8c0 00000001`3fba213e dopus+0x766d1
15 00000000`2c58f910 000007fe`fbd569a0 dopus+0x13213e
16 00000000`2c58f960 000007fe`fbd56877 COMCTL32!CallNextSubclassProc+0x8c
17 00000000`2c58f9e0 00000000`77319bd1 COMCTL32!MasterSubclassProc+0xe7
18 00000000`2c58fa80 00000000`773198da user32!UserCallWinProcCheckWow+0x1ad
19 00000000`2c58fb40 00000001`4011a1c8 user32!DispatchMessageWorker+0x3b5
1a 00000000`2c58fbc0 000007fe`f3a92211 dopus+0x6aa1c8
1b 00000000`2c58fc20 000007fe`f3ade92b dopuslib!IsWow64+0x31
1c 00000000`2c58fc50 000007fe`f3adeb76 dopuslib!DummyDllFunctionToAvoidSymbolConfusion+0x4a14b
1d 00000000`2c58fc80 00000000`7741652d dopuslib!DummyDllFunctionToAvoidSymbolConfusion+0x4a396
1e 00000000`2c58fcb0 00000000`7754c541 kernel32!BaseThreadInitThunk+0xd
1f 00000000`2c58fce0 00000000`00000000 ntdll!RtlUserThreadStart+0x1d
Now I had get this exception to (never get this before):
[code]Microsoft (R) Windows Debugger Version 6.12.0002.633 AMD64
*** wait with pending attachC:\LocalSymbols http://msdl.microsoft.com/download/symbols 3fcd0000 0000000140e5d000 C:\Program Files\GPSoftware\Directory Opus\dopus.exe77520000 00000000776c9000 C:\Windows\SYSTEM32\ntdll.dllf39e0000 000007fef3a4e000 C:\Windows\system32\verifier.dll77400000 000000007751f000 C:\Windows\system32\kernel32.dllfd500000 000007fefd56b000 C:\Windows\system32\KERNELBASE.dllfcc80000 000007fefcc9e000 C:\Windows\system32\USERENV.dllff3f0000 000007feff48f000 C:\Windows\system32\msvcrt.dllff4b0000 000007feff5dd000 C:\Windows\system32\RPCRT4.dllfd2d0000 000007fefd2df000 C:\Windows\system32\profapi.dllfcad0000 000007fefcadc000 C:\Windows\system32\VERSION.dllfd700000 000007fefd940000 C:\Windows\system32\WININET.dllfd6b0000 000007fefd6b4000 C:\Windows\system32\api-ms-win-downlevel-user32-l1-1-0.dll77300000 00000000773fa000 C:\Windows\system32\user32.DLLfdfe0000 000007fefe047000 C:\Windows\system32\GDI32.dllff5e0000 000007feff5ee000 C:\Windows\system32\LPK.dllff2f0000 000007feff3b9000 C:\Windows\system32\USP10.dllfd6a0000 000007fefd6a4000 C:\Windows\system32\api-ms-win-downlevel-shlwapi-l1-1-0.dllfd940000 000007fefd9b1000 C:\Windows\system32\shlwapi.DLLfd640000 000007fefd644000 C:\Windows\system32\api-ms-win-downlevel-version-l1-1-0.dllfd690000 000007fefd693000 C:\Windows\system32\api-ms-win-downlevel-normaliz-l1-1-0.dll776e0000 00000000776e3000 C:\Windows\system32\normaliz.DLLfdaf0000 000007fefdd99000 C:\Windows\system32\iertutil.dllfd610000 000007fefd615000 C:\Windows\system32\api-ms-win-downlevel-advapi32-l1-1-0.dllfdeb0000 000007fefdf8b000 C:\Windows\system32\advapi32.DLLff490000 000007feff4af000 C:\Windows\SYSTEM32\sechost.dllf92f0000 000007fef9308000 C:\Windows\system32\MPR.dllfa180000 000007fefa1bb000 C:\Windows\system32\WINMM.dllfdf90000 000007fefdfdd000 C:\Windows\system32\WS2_32.dllfda60000 000007fefda68000 C:\Windows\system32\NSI.dllfcaa0000 000007fefcac9000 C:\Windows\system32\MSVFW32.dllfe050000 000007fefedd8000 C:\Windows\system32\SHELL32.dllfbd30000 000007fefbf24000 C:\Windows\WinSxS\amd64_microsoft.windows.common-controls_6595b64144ccf1df_6.0.7601.17514_none_fa396087175ac9ac\COMCTL32.dllf9b90000 000007fef9baf000 C:\Windows\system32\AVIFIL32.dllff0e0000 000007feff2e3000 C:\Windows\system32\ole32.dllf2170000 000007fef2188000 C:\Windows\system32\MSACM32.dllff6d0000 000007feff82f000 C:\Windows\system32\urlmon.dllfd380000 000007fefd384000 C:\Windows\system32\api-ms-win-downlevel-ole32-l1-1-0.dll776f0000 00000000776f7000 C:\Windows\system32\PSAPI.DLLfad80000 000007fefad96000 C:\Windows\system32\NETAPI32.dllfad10000 000007fefad1c000 C:\Windows\system32\netutils.dllfd060000 000007fefd083000 C:\Windows\system32\srvcli.dllfacf0000 000007fefad05000 C:\Windows\system32\wkscli.dllfac10000 000007fefac24000 C:\Windows\system32\SAMCLI.DLLfb800000 000007fefb856000 C:\Windows\system32\UxTheme.dllfb5e0000 000007fefb7f6000 C:\Windows\WinSxS\amd64_microsoft.windows.gdiplus_6595b64144ccf1df_1.1.7601.18120_none_2b25b14c71ebf230\gdiplus.dllf1080000 000007fef127e000 C:\Windows\system32\query.dllff5f0000 000007feff6c7000 C:\Windows\system32\OLEAUT32.dllfcc10000 000007fefcc21000 C:\Windows\system32\WTSAPI32.dllfc630000 000007fefc68b000 C:\Windows\system32\DNSAPI.dllf3a50000 000007fef3bd7000 C:\Program Files\GPSoftware\Directory Opus\dopuslib.dllf5310000 000007fef5317000 C:\Windows\system32\SHFOLDER.dllfd390000 000007fefd4fc000 C:\Windows\system32\CRYPT32.dllfd370000 000007fefd37f000 C:\Windows\system32\MSASN1.dllf9990000 000007fef9a01000 C:\Windows\system32\WINSPOOL.DRVff3c0000 000007feff3ee000 C:\Windows\system32\IMM32.DLLfdda0000 000007fefdea9000 C:\Windows\system32\MSCTF.dllfcbf0000 000007fefcc08000 C:\Windows\system32\dwmapi.dllfa870000 000007fefa877000 C:\Windows\system32\msimg32.dllfd1c0000 000007fefd1cf000 C:\Windows\system32\CRYPTBASE.dllfb8e0000 000007fefba0c000 C:\Windows\system32\propsys.dllf8220000 000007fef8253000 C:\Windows\system32\rstrtmgr.dllfc930000 000007fefc97d000 C:\Windows\system32\ncrypt.dllfca00000 000007fefca22000 C:\Windows\system32\bcrypt.dllfd6c0000 000007fefd6fa000 C:\Windows\system32\wintrust.dllfb080000 000007fefb1e1000 C:\Windows\system32\WindowsCodecs.dllfd160000 000007fefd1b7000 C:\Windows\system32\apphelp.dllfee00000 000007fefee99000 C:\Windows\system32\CLBCatQ.DLLf5aa0000 000007fef5ad5000 C:\Windows\system32\EhStorShell.dllfeea0000 000007feff077000 C:\Windows\system32\SETUPAPI.dllfd650000 000007fefd686000 C:\Windows\system32\CFGMGR32.dllfd620000 000007fefd63a000 C:\Windows\system32\DEVOBJ.dllf5a20000 000007fef5aa0000 C:\Windows\system32\ntshrui.dllf6fe0000 000007fef6fef000 C:\Windows\system32\cscapi.dllfb280000 000007fefb28b000 C:\Windows\system32\slc.dllf62b0000 000007fef62b8000 C:\Windows\system32\IconCodecService.dllf3940000 000007fef39de000 C:\Windows\system32\riched20.dllfb860000 000007fefb88d000 C:\Windows\system32\ntmarta.dllff080000 000007feff0d2000 C:\Windows\system32\WLDAP32.dllfb460000 000007fefb495000 C:\Windows\system32\XmlLite.dllf6270000 000007fef627c000 C:\Windows\system32\LINKINFO.dllf5800000 000007fef5834000 C:\Windows\System32\shdocvw.dllfc800000 000007fefc817000 C:\Windows\system32\CRYPTSP.dllfc540000 000007fefc587000 C:\Windows\system32\rsaenh.dllfd2b0000 000007fefd2c4000 C:\Windows\system32\RpcRtRemote.dllfd270000 000007fefd2ad000 C:\Windows\system32\WINSTA.dllf0400000 000007fef0671000 C:\Windows\system32\wpdshext.dllf2910000 000007fef29cd000 C:\Windows\system32\PortableDeviceApi.dllf3050000 000007fef3125000 C:\Program Files\GPSoftware\Directory Opus\VFSPlugins\opus7zip.dllfd9c0000 000007fefda57000 C:\Windows\system32\COMDLG32.dllfd100000 000007fefd10b000 C:\Windows\system32\Secur32.dllfd130000 000007fefd155000 C:\Windows\system32\SSPICLI.DLLf72f0000 000007fef72f4000 C:\Windows\system32\api-ms-win-downlevel-advapi32-l2-1-0.dllf38d0000 000007fef3937000 C:\Program Files\GPSoftware\Directory Opus\dopusbch.dllfc7a0000 000007fefc7f5000 C:\Windows\system32\mswsock.dllfc980000 000007fefc987000 C:\Windows\System32\wship6.dllfb030000 000007fefb057000 C:\Windows\system32\IPHLPAPI.DLLfb020000 000007fefb02b000 C:\Windows\system32\WINNSI.DLLf5f70000 000007fef5f74000 C:\Windows\system32\api-ms-win-downlevel-shlwapi-l2-1-0.dllfede0000 000007fefedf9000 C:\Windows\system32\imagehlp.dllfc4a0000 000007fefc4ec000 C:\Windows\system32\bcryptprimitives.dllf3be0000 000007fef3d7c000 C:\Windows\system32\NetworkExplorer.dllf6bb0000 000007fef6bba000 C:\Windows\System32\drprov.dllf6350000 000007fef6372000 C:\Windows\System32\ntlanman.dllf6330000 000007fef634d000 C:\Windows\System32\davclnt.dllf62a0000 000007fef62aa000 C:\Windows\System32\DAVHLPR.dllf38a0000 000007fef38c7000 C:\Windows\system32\EhStorAPI.dllfd1d0000 000007fefd261000 C:\Windows\system32\SXS.DLLfac30000 000007fefac9e000 C:\Program Files\GPSoftware\Directory Opus\dopushlp.dll0e980000 000000000e9d1000 C:\Program Files\GPSoftware\Directory Opus\Viewers\gifanim.dllf2fe0000 000007fef3045000 C:\Program Files\GPSoftware\Directory Opus\Viewers\movie.dllf81f0000 000007fef821b000 C:\Program Files\GPSoftware\Directory Opus\Viewers\wma.dllf0110000 000007fef03f6000 C:\Windows\system32\WMVCore.DLLf6e50000 000007fef6e9d000 C:\Windows\system32\WMASF.DLLf1aa0000 000007fef1b91000 C:\Windows\system32\ddraw.dllf8560000 000007fef8568000 C:\Windows\system32\DCIMAN32.dllf8010000 000007fef802c000 C:\Program Files\GPSoftware\Directory Opus\Viewers\pcx.dllf6390000 000007fef63bf000 C:\Program Files\GPSoftware\Directory Opus\Viewers\targa.dllf2450000 000007fef248c000 C:\Program Files\GPSoftware\Directory Opus\Viewers\audiotags.dllf1fa0000 000007fef207f000 C:\Program Files\GPSoftware\Directory Opus\Viewers\dcrawrap.dllf21c0000 000007fef21f2000 C:\Program Files\GPSoftware\Directory Opus\Viewers\j2k.dllf5270000 000007fef52a0000 C:\Program Files\GPSoftware\Directory Opus\Viewers\wav.dllf1f30000 000007fef1f94000 C:\Program Files\GPSoftware\Directory Opus\Viewers\docs.dllf1a60000 000007fef1a94000 C:\Program Files\GPSoftware\Directory Opus\Viewers\multiview.dllf1a10000 000007fef1a5d000 C:\Program Files\GPSoftware\Directory Opus\Viewers\textthumb.dllf19c0000 000007fef1a0e000 C:\Program Files\GPSoftware\Directory Opus\Viewers\text.dllfcc60000 000007fefcc7b000 C:\Windows\system32\GPAPI.dllfaee0000 000007fefaef1000 C:\Windows\system32\dhcpcsvc6.DLLfaec0000 000007fefaed8000 C:\Windows\system32\dhcpcsvc.DLLfcae0000 000007fefcae7000 C:\Windows\System32\wshtcpip.dll77570590 cc int 3 0:031> g Sun Apr 6 09:30:25.239 2014 (UTC + 2:00): ModLoad: 000007fef1690000 000007fe`f16ed000 C:\Windows\system32\zipfldr.dll
===========================================================
00000000019B1000 : Heap handle
0000000056B32FB0 : Heap block
000000000000004E : Block size
0000000056B32F88 : Corruption Address
Sun Apr 6 09:30:30.866 2014 (UTC + 2:00): ===========================================================
Sun Apr 6 09:30:30.866 2014 (UTC + 2:00): (ce0.eb0): Break instruction exception - code 80000003 (first chance)
# Child-SP RetAddr Call Site
00 00000000`2c51dcb0 000007fe`f39e92da verifier!VerifierStopMessage+0x1f0
01 00000000`2c51dd60 000007fe`f39e9656 verifier!AVrfpDphReportCorruptedBlock+0x112
02 00000000`2c51de20 000007fe`f39e6d2d verifier!AVrfpDphCheckPageHeapBlock+0xfe
03 00000000`2c51dea0 000007fe`f39e6e45 verifier!AVrfpDphFindBusyMemory+0xdd
04 00000000`2c51dee0 000007fe`f39e870e verifier!AVrfpDphFindBusyMemoryAndRemoveFromBusyList+0x25
05 00000000`2c51df10 00000000`775e99b5 verifier!AVrfDebugPageHeapFree+0x8a
06 00000000`2c51df70 00000000`7758db50 ntdll!RtlDebugFreeHeap+0x35
07 00000000`2c51dfd0 00000000`775740fd ntdll! ?? ::FNODOBFM::`string'+0x10b82
08 00000000`2c51e310 00000000`7742300a ntdll!RtlFreeHeap+0x1a6
09 00000000`2c51e390 00000001`406523f8 kernel32!HeapFree+0xa
0a 00000000`2c51e3c0 00000001`401ef06d dopus!DummyExeFunction1ToAvoidSymbolConfusion+0x1d9028
0b 00000000`2c51e3f0 00000001`3ff1b8a8 dopus+0x51f06d
0c 00000000`2c51e420 00000001`3ff1b8e8 dopus+0x24b8a8
0d 00000000`2c51e450 00000001`400c3503 dopus+0x24b8e8
0e 00000000`2c51e480 00000001`3fe775c7 dopus+0x3f3503
0f 00000000`2c51e4b0 00000001`3ff0a2d3 dopus+0x1a75c7
10 00000000`2c51e520 00000001`3ff02069 dopus+0x23a2d3
11 00000000`2c51e560 00000000`77319bd1 dopus+0x232069
12 00000000`2c51ed00 00000000`773172cb user32!UserCallWinProcCheckWow+0x1ad
13 00000000`2c51edc0 00000000`77316829 user32!DispatchClientMessage+0xc3
14 00000000`2c51ee20 00000000`775711f5 user32!_fnDWORD+0x2d
15 00000000`2c51ee80 00000000`7730cbfa ntdll!KiUserCallbackDispatcherContinue
16 00000000`2c51ef08 00000001`3ff0353a user32!NtUserDestroyWindow+0xa
17 00000000`2c51ef10 00000000`77319bd1 dopus+0x23353a
18 00000000`2c51f6b0 00000000`773198da user32!UserCallWinProcCheckWow+0x1ad
19 00000000`2c51f770 00000001`4037a1c8 user32!DispatchMessageWorker+0x3b5
1a 00000000`2c51f7f0 000007fe`f3a92211 dopus+0x6aa1c8
1b 00000000`2c51f850 000007fe`f3ade92b dopuslib!IsWow64+0x31
1c 00000000`2c51f880 000007fe`f3adeb76 dopuslib!DummyDllFunctionToAvoidSymbolConfusion+0x4a14b
1d 00000000`2c51f8b0 00000000`7741652d dopuslib!DummyDllFunctionToAvoidSymbolConfusion+0x4a396
1e 00000000`2c51f8e0 00000000`7754c541 kernel32!BaseThreadInitThunk+0xd
1f 00000000`2c51f910 00000000`00000000 ntdll!RtlUserThreadStart+0x1d
Leo
April 6, 2014, 7:59am
7
The "first chance exception" things are normal and can be ignored. They're part of how Windows works.
The last code block looks interesting, though.
Is a crash dump created, or can one be saved from WinDbg?
No, there is no dump file for this time. It looks like I need to generate one manually with the .dump command inside of WinDbg.
What for settings can help you best? (msdn.microsoft.com/en-us/library ... 85%29.aspx )
Just for info: if I try to ignore the first exception and press F5 to continue, then the same exception will come as "second change exception" unlimited times again. So I can't work with DO after this.
Leo
April 6, 2014, 9:17am
10
/ma or, if that produces something too large, /f should be best.
Please zip and email the dmp to leo@gpsoft.com.au
Just to be sure. Did you get all my 4 e-mails? (2x 06.04, 12.05, 15.06)
Leo
April 18, 2014, 8:36am
12
Yes, I got them. Will reply as soon as I have a chance to investigate in detail.
Leo
April 30, 2014, 8:21pm
13
This was a bug on our side and has now been fixed internally.
Many thanks for all your help with this, in particular the crash dumps which helped us pinpoint the problem.
We're about to put out 11.4 which won't contain the fix, but shortly after that we will put out an 11.4.1 beta version which will contain it.